Hey everybody, this is my first post on this website 👋🏻.
In this post, I'll show you how to:
👉🏻 Install the Damn Vulnerable Web Application (DVWA) using XAMPP on Windows, a popular setup for practicing web security skills...
👉🏻 Set up Wazuh to monitor DVWA’s logs, helping you analyze potential attacks in a controlled environmentBefore we get started.. what is DVWA?
DVWA is a PHP/MySQL web application designed to be vulnerable. It’s a fantastic tool for security professionals, web developers, and students to practice identifying and exploiting common web vulnerabilities like SQL Injection and Cross-Site Scripting (XSS) in a legal, safe environment.
1️⃣ Installing DVWA with XAMPP on Windows
Let’s set up DVWA using XAMPP, a free and open-source web server solution that includes Apache, MariaDB, and PHP. Follow these steps:
- Download and Install XAMPP: Head to the official XAMPP website and download the Windows installer.
 Run the installer, selecting Apache and MySQL as components along with phpMyAdmin ticked as well, and complete the setup. Once installed, open the XAMPP Control Panel and start the Apache and MySQL services.
Run the installer, selecting Apache and MySQL as components along with phpMyAdmin ticked as well, and complete the setup. Once installed, open the XAMPP Control Panel and start the Apache and MySQL services. - Download DVWA: Visit the official DVWA GitHub repository and download the ZIP file by clicking the “Code” button and selecting “Download ZIP.”
 Extract the ZIP file to a folder named
Extract the ZIP file to a folder named dvwa. - Move DVWA to XAMPP’s htdocs: Copy the extracted
dvwafolder to XAMPP’shtdocsdirectory, typically located atC:\xampp\htdocs\. - Configure DVWA: Navigate to
C:\xampp\htdocs\dvwa\config. You’ll find a file namedconfig.inc.php.dist. Rename it toconfig.inc.php. Open the file in a text editor (e.g., Notepad) and locate the line with the database password. Since XAMPP’s default MySQL password is empty, set the password to blank by editing the line to:$_DVWA['db_password'] = '';. Save the file. - Access DVWA in Your Browser: Open your browser and navigate to
http://127.0.0.1/dvwa/. You’ll see a setup page.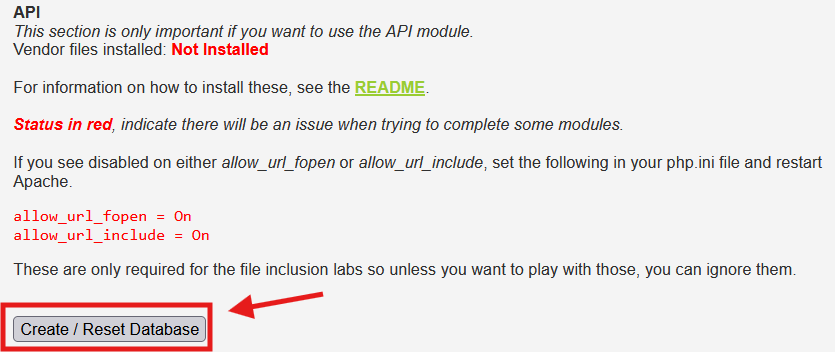 Scroll down and click “Create / Reset Database” to initialize the DVWA database. After a moment, you’ll be redirected to the login page.
Scroll down and click “Create / Reset Database” to initialize the DVWA database. After a moment, you’ll be redirected to the login page. - Log In to DVWA: Use the default credentials—username:
admin, password:password. Once logged in, you can explore vulnerabilities like SQL Injection and XSS at different difficulty levels.
2️⃣ Setting Up Wazuh to Monitor DVWA Logs
Wazuh is a powerful open-source security monitoring platform that can help you analyze logs for potential security events. Since DVWA runs on Apache (via XAMPP), we’ll configure Wazuh to monitor Apache’s access and error logs, which will include DVWA activity.
- Install Wazuh: Wazuh can be deployed in various ways, but for simplicity, I recommend using the pre-built Wazuh OVA (a virtual appliance). Download the latest Wazuh OVA from the Wazuh website and import it into a virtualization tool like VirtualBox. Follow the setup instructions to get the Wazuh manager running. Note the manager’s IP address (e.g.,
192.168.1.100). - Install the Wazuh Agent on Your Windows Machine: Download the Wazuh agent for Windows from the Wazuh website. Run the installer, and when prompted, enter the Wazuh manager’s IP address to connect the agent to the manager. Complete the installation and ensure the agent service is running.
- Configure the Wazuh Agent to Monitor Apache Logs: On your Windows machine, locate the Wazuh agent configuration file at
C:\Program Files (x86)\ossec-agent\ossec.conf. Open it in a text editor with administrator privileges. Add the following block to monitor Apache logs generated by XAMPP:
Save the file and restart the Wazuh agent service via the Services app or by running<localfile> <log_format>syslog</log_format> <location>C:\xampp\apache\logs\access.log</location> </localfile> <localfile> <log_format>syslog</log_format> <location>C:\xampp\apache\logs\error.log</location> </localfile>net stop wazuhandnet start wazuhin an elevated Command Prompt. - Simulate Activity in DVWA: Back in DVWA, perform some actions like attempting an SQL Injection (e.g., entering
' OR '1'='1in a login field) or navigating through different pages.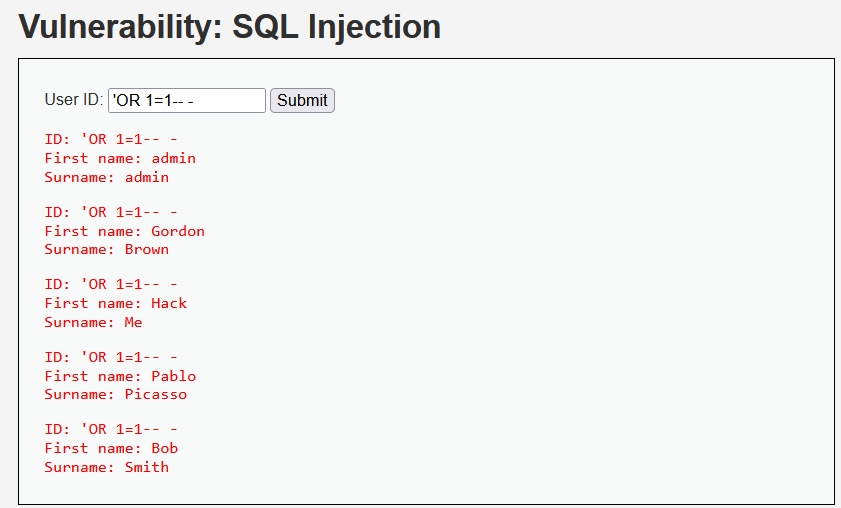 These actions will generate entries in Apache’s access and error logs.
These actions will generate entries in Apache’s access and error logs.
3️⃣ Reading DVWA Logs in Wazuh
Now that the Wazuh agent is sending Apache logs to the Wazuh manager, let’s view them in the Wazuh dashboard.
- Access the Wazuh Dashboard: Open a browser and navigate to your Wazuh manager’s dashboard (e.g.,
https://192.168.1.100:5601if using the default Kibana port). Log in with the default credentials (usuallyadminand a password set during setup). - View the Logs: In the Wazuh dashboard, go to the “Security Events” or “Discover” tab. Filter the logs by selecting the index pattern (e.g.,
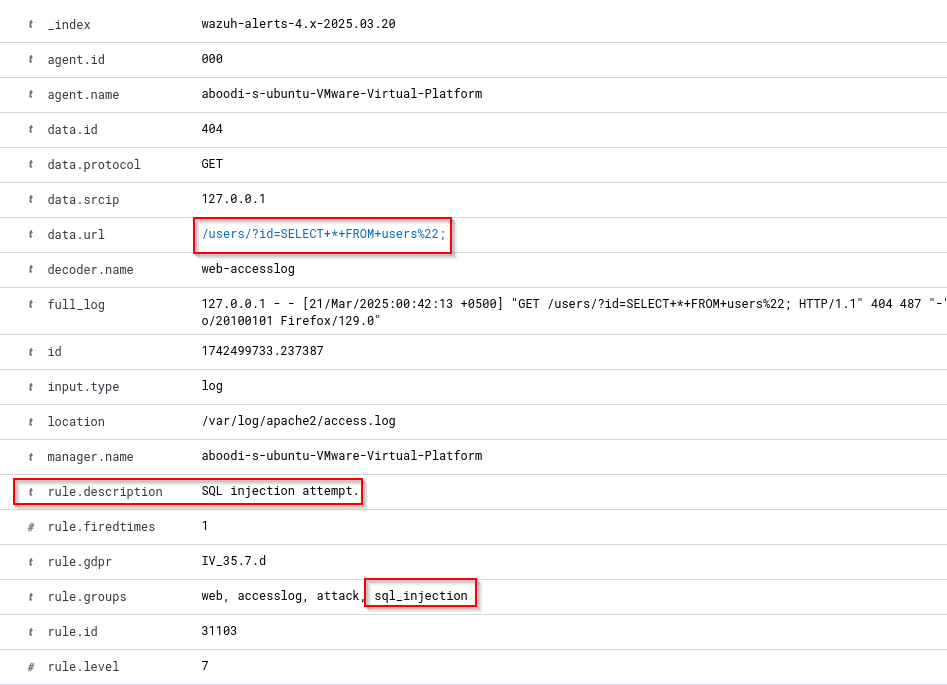
wazuh-alerts-*). You can search for logs from your Windows machine by filtering with the agent’s name or IP. Look for entries related toaccess.logorerror.log. For example, you might see HTTP requests to/dvwa/paths, including any malicious inputs you tried. - Analyze the Logs: Wazuh will parse the logs and may generate alerts if it detects suspicious activity (e.g., repeated failed login attempts). Use the dashboard to analyze trends, such as the frequency of requests or errors related to specific DVWA vulnerabilities.
Conclusion ✅

By following this guide, you’ve set up DVWA using XAMPP to practice web security and configured Wazuh to monitor its logs. This setup allows you to experiment with vulnerabilities in a safe environment while learning how to use a SIEM tool like Wazuh to detect and analyze potential attacks. For more resources, check out the OWASP website for web security best practices and the Wazuh documentation for advanced log analysis techniques.